Forklift Upgrade Arch Linux To A Dell Precision 3561
date: 2021-10-19
Introduction
I fork-lift upgraded my luks-encrypted Arch Linux installation from a Lenovo T460 to a luks-encrypted, software raid1 mirror on a Dell Precision 3561.
It was relatively easy to do.
The New Laptop
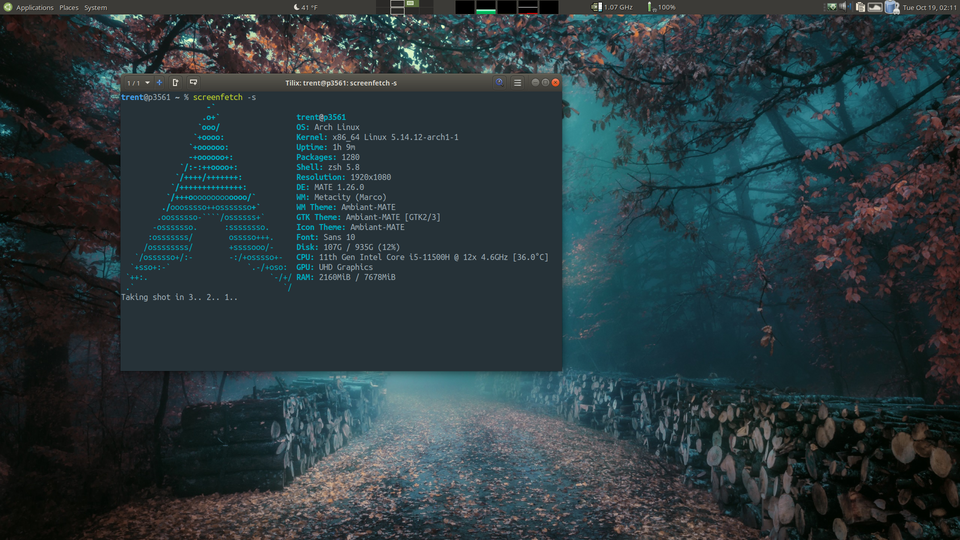
I ordered a new Dell Precision 3561 with the minimal ram and ssd configuration, running Ubuntu 20.04.
The plan was to transfer a luks-encrypted Arch Linux from my Lenovo T460 to a luks-encrypted thumbdrive. Then run Arch Linux from the thumbdrive on the new Precision 3561 for a few days while I waited for Amazon to deliver some 1tb Samsung 830 nvme ssds. And then finally to transfer the Arch installation from the thumbdrive onto an luks-encrypted software raid1 mirror on the new Precision 3561.
Everything went according to plan, with not a single stumble or mishap; and so I'm documenting here how it went down. The only thing left to do now is to order 64gb of ram, so I can run Android Studio, and continue working on my Android App (which needs some work). And of course update Arch Linux 5 times a day.
I use Arch Linux, btw!
Creating a Rescue Disk
The transfer process I came up with involved two thumb drives: one to serve as a live disk to work from, and the other to temporarily run Arch on the new laptop.
So why would I not use an Arch install disk as a live disk? Because I cache Arch packages on my lan using an Nginx reverse-cacheing proxy, which makes it really fast to simply bootstrap (pacstrap) a new Arch installation onto a thumb drive, exactly as I would install Arch anywhere else.
Transfering Arch to USB
I booted my old T460 from my rescue disk and also plugged the other thumb drive into a usb port.
Formatting the Thumb Drive.
I opened the target thumbdrive in gdisk interactive partition tool, created a new
gpt partition table by pressing o. Then created a 1GB efi partition, type ef00,
and a single partition for the remainder of the 256gb thumb.
- I formatted the efi parition on the thumbdrive:
mkfs.vfat -F32 /dev/sdc1
- I luks-encrypted the other partition on the thumbdrive:
luksFormat -y -v /dev/sdc2
- Then I opened the new luks device:
cryptsetup open /dev/sdc2 cryptroot
- And formatted it:
mkfs.xfs /dev/mapper/cryptroot
Copying the efi partition files to Thumb Drive
More specifically in a typical systemd-boot configuration the efi partition
contains the entire /boot directory.
- I mounted the T460's efi partition for Arch Linux:
mount /dev/sda5 /mnt2
- I mounted the thumbdrive's efi partition:
mount /dev/sdc1 /mnt
- And then copied all the files over:
cp -av /mnt2/* /mnt/
- I then unmounted the efi partitions:
umount /mnt2 ; umount /mnt
Copying the / partition files to the Thumb Drive
- I decrypted the Arch
/device on the T460cryptsetup open /dev/sda6 cryptroot2
- And then mounted it:
mount /dev/mapper/cryptroot2 /mnt2
- ...mounted the
/device for the thumbdrive:mount /dev/mapper/cryptroot /mnt
- And copied the files:
rsync -aAXvPH /mnt2/ /mnt/
Rescuing The Thumb Drive via Chroot
- I unmounted the T460's
/device:umount /mnt2
- Mounted the thumbdrive's efi partition relative to
/mntmount /dev/sdc /mnt/boot
- And entered chroot:
arch-chroot /mnt
Updating fstab for the Thumb Drive
- I located the UUID of the thumbdrive's efi partition:
blkid /dev/sdc1
- I located the UUID of the luks device:
blkid /dev/mapper/cryptroot
- And updated
/etc/fstabaccordingly.
# /etc/fstab
# /dev/mapper/cryptroot
UUID=391f6062-d8af-4266-a48c-186270d54ef3 / xfs rw,relatime,attr2,inode64,logbufs=8,logbsize=32k,noquota 0 1
# /dev/sdc1
UUID="FACA-0B61" /boot vfat rw,relatime,fmask=0022,dmask=0022,codepage=437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 2
...
Rebuilding the Initramfs for the Thumb Drive
Still inside chroot I ran the following command to rebuild the initramfs.
mkinitcpio -P
Updating the systemd-boot Entry for the Thumb Drive
- I located the UUID of
/dev/sdc2with the following command:blkid /dev/sdc2
- And updated
/boot/loader/entries/arch.confaccordingly.
# /boot/loader/entries/arch.conf
title arch
linux /vmlinuz-linux
initrd /intel-ucode.img
initrd /initramfs-linux.img
options cryptdevice=UUID=f8c5062a-849d-4c56-bc98-2c93da85090f:cryptroot root=/dev/mapper/cryptroot rw quiet loglevel=3
Running Arch from USB
At this point Arch would boot and run flawlessly on the new Dell Precision 3561. I went ahead and changed the hostname, machine-id, ssh-keys, and host_ssh_keys to make it official.
While test-driving the new machine, I worked on my Ansible-KVM Router Lab. As configured, the mobile workstation gets great battery life under a light work-load of web browser and ssh terminal work.
Satisfied that the new system was going to work out, I ordered a pair of 1tb Samsung 830 nvme ssds, and installed them when they arrived.
Transfering Arch to the New ssds
After installing new nvme ssds, I booted the Dell Precision 3561 from my rescue disk, and also plugged in the thumbdrive on which my Arch system was installed.
Formatting The New NVME ssds
I opened each nvme ssd in gdisk, created a new gpt partition table,
an 1GB efi partition (type ef00), and for the remainder of each disk
created a Linux Raid Parition (type fd00).
- I formatted one of the efi partitions:
mkfs.vfat -F32 /dev/nvme0n1p1
- I created a raid array:
mdadm --create --verbose --level=1 --metadata=1.2 \ --raid-devices=2 /dev/md0 /dev/nvme0n1p2 /dev/nvme1n1p2 - I luks-encrypted the new raid array:
luksFormat -y -v /dev/md0
- I opened the new luks device:
cryptsetup open /dev/md0 cryptroot
- And then Formatted it:
mkfs.xfs /dev/mapper/cryptroot
Copying the efi partition files to NVME ssd
- I mounted the thumbdrive's efi partition:
mount /dev/sdb1 /mnt2
- Then I mounted the laptop's efi partition:
mount /dev/nvme0n1p1 /mnt
- And copied to files to the new efi partition:
cp -av /mnt2/* /mnt/
- And then I unmounted both efi partitions:
umount /mnt2 ; umount /mnt
Copying the / partition files to the new NVME ssds
- First I opened the
/luks device on the thumbdrive:cryptsetup open /dev/sdb2 cryptroot2
- And then mounted it:
mount /dev/mapper/cryptroot2 /mnt2
- Then I mounted the laptop's
/luks device:mount /dev/mapper/cryptroot /mnt
- And
rsyncedthe operating system files onto the new laptop:rsync -aAXvPH /mnt2/ /mnt/
Rescuing The New Laptop via Chroot
- First I unmounted the thumbdrive:
umount /mnt2
- Then I mounted the efi partition relative to
/mnt:mount /dev/nvme0n1p1 /mnt/boot
- And entered chroot;
arch-chroot /mnt
Updating fstab for The New Laptop
- I used to the following command to discover the UUID of the
/device:blkid /dev/mapper/cryptroot
- And a similar command to find the UUID of the efi partition:
blkid /dev/nvme0n1p1
- Then I editted
/etc/fstabto describe the above two UUIDs.
# /etc/fstab
# /dev/mapper/cryptroot
UUID=3486b7d1-ccc9-43dc-b8ab-abcf71aea90f / xfs rw,relatime,attr2,inode64,logbufs=8,logbsize=32k,sunit=32,swidth=256,noquota 0 1
# /dev/nvme0n1p1
UUID=9FE0-2A98 /boot vfat rw,relatime,fmask=0022,dmask=0022,codepage=437,iocharset=ascii,shortname=mixed,utf8,errors=remount-ro 0 2
...
Updating mdadm.conf and mkinitcpio.conf
When I boot the laptop, the initramfs must assemble the raid array, which requires the following configuration details.
I appended a description of the raid array to the bottom of /etc/mdadm.conf by
running the following command.
mdadm --detail --scan >> /etc/mdadm.conf
Then I editted /etc/mkinitcpio.conf to require the mdadm_udev hook.
# /etc/mkinitcpio.conf
...
# change this
HOOKS=(base udev autodetect modconf block encrypt filesystems keyboard fsck)
# to this
HOOKS=(base udev autodetect modconf block mdadm_udev encrypt filesystems keyboard fsck)
...
mkinitcpio -P
Updating the systemd-boot Entry for the New Laptop
The final step was to update /boot/loader/entries/arch.conf.
As explained above, the initramfs assembles the raid device,
so I just need to tell the kernel about it.
I used the following command to discover the UUID of the raid1 device:
blkid /dev/md0
And then updated /boot/loader/entries/arch.conf accordingly.
title arch
linux /vmlinuz-linux
initrd /intel-ucode.img
initrd /initramfs-linux.img
options cryptdevice=UUID=48f782a9-6c1b-4242-84f9-66b20ff27845:cryptroot root=/dev/mapper/cryptroot rw quiet loglevel=3